After the first public demonstration of our new Trusted Zero Client technology at NATO Edge last October, our partners are now bringing their next-generation Trusted Zero Clients to market. Designed with zero trust architecture security features and managed by the new Anyware Trust Center, Trusted Zero Clients take a big leap forward in security, with the latest PC-over-IP (PCoIP®) protocol features and PCoIP® Ultra performance.
Holistic Zero Trust is a critical defence against cyberthreats, especially in today’s hybrid work environment. The added demand for remote access to corporate applications comes with a heightened concern over data security.
Most products typically address siloed segments, such as network or endpoint security, identity, or data security. But it’s important to note that digital workspaces and hybrid work reach across these security segments, requiring close alignment between various security and IT teams in addition to interoperability between security tools.
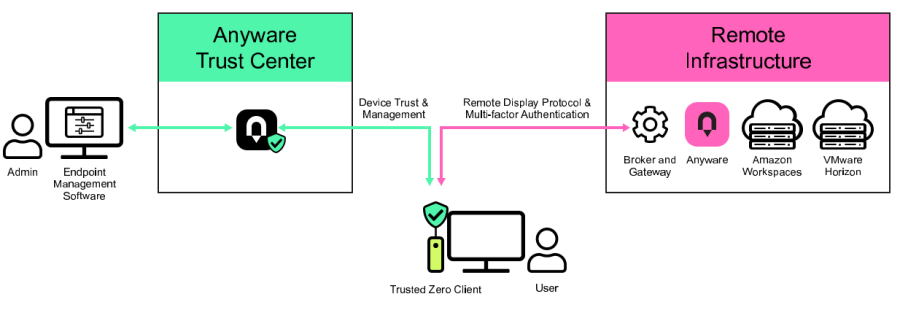
Trusted Zero Clients managed by the Anyware Trust Center provide a new level of Zero Trust device security to improve cybersecurity posture and build a foundation for corporate-wide trusted digital workspaces.
Trusted Zero Clients are the first endpoint offerings to interface with Anyware Trust Center
HP has also launched the Anyware Trust Center, which adds an additional security layer to monitor devices connected with Anyware software, first starting with the ability to set policy controls remotely onto Trusted Zero Clients based on zero trust principles.
The Anyware Trust Center zero trust policy engine for digital workspaces enables a more secure way to manage and monitor Trusted endpoints. Anyware Trust Center is a service component that is installed in the end customer’s environment. Interfacing with endpoint management tools, the Anyware Trust Center helps ensure Trusted endpoints and components adhere to security policies by providing real-time responses to policy incidents. For more information, visit: Anyware Trust Center.
Trusted Zero Clients for Your Zero Trust Architecture
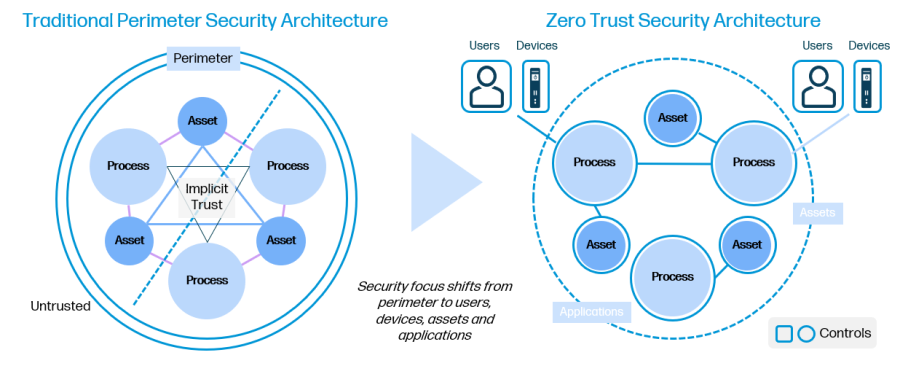
Zero Trust is a strategy (and bundle of technologies) that replaces traditional perimeter-based security with a model focused on users, devices, applications, and assets. Users are not provided blanket access to applications, services, and files; they can only access the resources needed for a given task or function. Even within the company network, devices and users undergo verification and authentication checks at several points before accessing company data.
Extending trust principles beyond mere network access goes a long way towards improving enterprise security. By requiring users and devices to authenticate themselves continuously and limiting resource access to only the files and data they need for the given task, users and devices are less vulnerable to hackers.
Built on Secured PCoIP Technology
Trusted Zero Clients are factory-authenticated devices, equipped with the latest PCoIP protocol features and improved PCoIP Ultra performance to deliver a secure, high-definition and highly responsive computing experience, even for the most demanding use cases. PCoIP technology uses advanced display compression to allow users remote access to their on-premises workstations or virtual machine instances in local data centers or public clouds from a broad range of endpoint devices.
Other protocols offer additional brute force lossless modes to overcome compression artifacts – these typically burden network or compute resources, resulting in throttled throughput and compromised interactivity. But with PCoIP technology, there is little difference for the user between working with a local computer or from a remote endpoint receiving a PCoIP streamed pixel representation of their desktop and applications. And from an IT perspective, remote desktops are more secure, as no data ever leaves the corporate environment.
Trusted Zero Client Availability
Trusted Zero Clients will be available in a variety of form factors from our partners including 10ZiG Technology Ltd., Amulet Hotkey, Atrust, ClearCube, ELSA, HP Inc., NCS Technologies Inc., Rangee GmbH, TriCIS, VXL and Zenk GmbH. Contact your preferred supplier for more information about product specifications and availability.