Release Notes
Anyware Trust Center
25.06.0
Release 25.06 of the Anyware Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following:
Darksite Downloads Now Available Through Two IP Addresses
Previously, darksite bundles were downloaded via dl.anyware.hp.com and utilized the global Content Delivery Network (CDN), requiring multiple IP addresses to be allowlisted. With version 25.03.5, darksite bundles will be downloaded through the prod.onboarding.hydra.teradici.com subdomain. This change simplifies allowlisting, as only the following two US-based IP addresses are now required:
- 166.117.189.248
- 166.117.55.125
Non-darksite (internet connected) installations continue to use the CDN, benefiting from its capabilities of supporting regionally distributed downloads. For more information, see Updating the config.yaml file.
Support for Manual Renewal of Registration Certificates
Version 25.06 of the Anyware Trust Center introduces support for manual renewal of registration certificates. This manual process is necessary if your Trust Center is installed in a darksite, or cannot utilize the automatic renewal mechanism. In the absence of a manual renewal process, Trust Center installed in darksite environments would become invalid. The ability to manually renew registration certificates ensures these Trust Center deployments stay both functional and secure.
For more information, see the Manually Renew the Trust Center Registration Certificate topic.
Support for Automatic Renewal of Registration Certificates
With version 25.06, Anyware Trust Center now automatically renews registration certificates. If Anyware Trust Center is internet-connected, registration certificates are renewed automatically 60 days before they expire. This ensures Trust Center deployments stay functional, without service interruptions.
Optional Connectivity for Trusted Zero Clients
Version 25.06 now supports using Trusted Zero Clients without a Trust Center connection, making it ideal for proof-of-concepts, evaluations, and air-gapped minimal environments. In this scenario, Trusted Zero clients will operate with a reduced feature set, and Trusted Zero Clients connecting to hosts will only be secured by the PCoIP protocol. The Trust Center is required if remote management, observability, end-to-end trust, and security policy enforcement is desired.
The ability to connect to Trust Center is fully controlled from the Settings menu of the Trusted Zero Clients. For more information, see the Trusted Zero Client guide.
Notifications for Scheduled Power Events
In version 25.06, support has been added for notifications in event of scheduled power events, such as reboot of Trusted Zero clients. Previously, scheduled reboots were not accompanied by notifications, resulting in abrupt interruption of user work. Now, a warning will appear up to 5 minutes before reboot, giving users time to save their work.
Info:
Trusted Zero Clients are updated using the over-the-air (OTA) updates sent by the Trust Center they are connected to. If a Trusted Zero Client is not registered to a Trust Center, OTA updates will not be available. As a result, Trusted Zero Clients cannot be updated.
25.03.5
Note:
Anyware Trust Center 25.03 skipped two patch versions, making 25.03.4 the release immediately following 25.03.1.
Version 25.03.5 of the Anyware Trust Center is a maintenance release that replaces and deprecates 25.03.4. In addition, the following new feature has been introduced:
Darksite Downloads Now Available Through Two IP Addresses
Previously, Darksite bundles were downloaded via dl.anyware.hp.com and utilized the global Content Delivery Network (CDN), requiring multiple IP addresses to be allowlisted. With version 25.03.5, darksite bundles will be downloaded through the subdomains of prod.onboarding.hydra.teradici.com. This change simplifies allowlisting, as only the following two US-based IP addresses are now required:
- 166.117.189.248
- 166.117.55.125
Non-darksite (internet connected) installations continue to use the CDN, benefiting from its capabilities of supporting regionally distributed downloads.
Previous Releases in This Version
25.03.4
Version 25.03.4 of the Anyware Trust Center is a maintenance release that replaces and deprecates 25.03.1.
25.03.1
Support for MongoDB 5.x
Trust Center has updated it's internal Mongo DB instance to version 5.x, which requires the AVX CPU extension. Therefore, machines without AVX support can no longer successfully deploy a new Trust Center or upgrade an existing Trust Center to 25.03.0.
25.03.0
Version 25.03.0 of the Anyware Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following:
Support for Imprivata Authentication
Version 25.03 of the Anyware Trust Center supports Imprivata OneSign for authenticating Trusted Zero Clients connecting to Horizon hosts. Imprivata OneSign enables users to access corporate networks, desktops, and applications with a single sign on. This reduces the need for maintaining separate passwords and prevents unauthorized access.
For more information, see Enabling Imprivata Authentication.
Trust Center Installation with DISA STIGs
In version 25.03, support has been added to enable the installation of the Trust Center on servers and virtual machines that comply with the security policies and configurations recommended by the US DOD Cyber Exchange. For this purpose, a new configuration called `fapolicyd` has been added, which allows the Trust Center components to run on servers that adhere to STIG requirements. For more information see Trust Center Installation with DISA STIGs.
SIPR/NIPR Network Migration
In version 25.03, support has been added for securely migrating Trusted Zero Clients between SIPR, NIPR, and insecure networks. When re-commissioning a Trusted Zero Client for use on a SIPR/NIPR or insecure network, specific steps must be followed to completely erase all local data and configurations. This prevents accidental or malicious access to critical data during network migrations, and ensures compliance with security recommendations.
Support for Darksite Upgrades
Version 25.03 now supports upgrade of Trust Center that does not have a connection to the public internet. Upgrading a dark site requires a temporary internet-connected machine, which downloads the required packages to create an upgrade bundle. The upgrade bundle is transferred to the dark site machine and used for upgrading Trust Center.
The dark site installer for 25.03 also includes a few changes from how the commands are run, from the original 24.07 release.
For more information, see Darksite Upgrade of Trust Center.
Support for Uploading OTA packages to Darksite Trust Center
As Darksite Trust Center operates without internet connectivity, automatic OTA updates are not possible. Version 25.03 addresses this limitation by introducing a new command for managing firmware within the Trust Center. Administrators can now download as well as upload OTA packages to the Trust Center server without the need for opening an internet connection.
For more information see the following topics:
MariaDB Requirement Removed
In version 25.03, MariaDB has been merged into MongoDB. As a result, MariaDB is no longer deployed with the Trust Center. This simplifies end-user management of persistent stores and reduces memory and CPU footprint within the Trust Center.
Other Update
To limit the amount of sensitive data saved into Anyware Trust Center support bundles, the auto-generated Trust Center admin password, typically used as the default password, will no longer be saved to the configuration file. This limits the exposure of sensitive data, and prevents its accidental access.
25.03.4
Version 25.03.4 of the Anyware Trust Center is a maintenance release that replaces and deprecates 25.03.1.
Note:
Anyware Trust Center 25.03 skipped two patch versions, making 25.03.4 the release immediately following 25.03.1.
Previous Releases in This Version
25.03.1
Support for MongoDB 5.x
Trust Center has updated it's internal Mongo DB instance to version 5.x, which requires the AVX CPU extension. Therefore, machines without AVX support can no longer successfully deploy a new Trust Center or upgrade an existing Trust Center to 25.03.0.
25.03.0
Version 25.03.0 of the Anyware Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following:
Support for Imprivata Authentication
Version 25.03 of the Anyware Trust Center supports Imprivata OneSign for authenticating Trusted Zero Clients connecting to Horizon hosts. Imprivata OneSign enables users to access corporate networks, desktops, and applications with a single sign on. This reduces the need for maintaining separate passwords and prevents unauthorized access.
For more information, see Enabling Imprivata Authentication.
Trust Center Installation with DISA STIGs
In version 25.03, support has been added to enable the installation of the Trust Center on servers and virtual machines that comply with the security policies and configurations recommended by the US DOD Cyber Exchange. For this purpose, a new configuration called `fapolicyd` has been added, which allows the Trust Center components to run on servers that adhere to STIG requirements. For more information see Trust Center Installation with DISA STIGs.
SIPR/NIPR Network Migration
In version 25.03, support has been added for securely migrating Trusted Zero Clients between SIPR, NIPR, and insecure networks. When re-commissioning a Trusted Zero Client for use on a SIPR/NIPR or insecure network, specific steps must be followed to completely erase all local data and configurations. This prevents accidental or malicious access to critical data during network migrations, and ensures compliance with security recommendations.
Support for Darksite Upgrades
Version 25.03 now supports upgrade of Trust Center that does not have a connection to the public internet. Upgrading a dark site requires a temporary internet-connected machine, which downloads the required packages to create an upgrade bundle. The upgrade bundle is transferred to the dark site machine and used for upgrading Trust Center.
The dark site installer for 25.03 also includes a few changes from how the commands are run, from the original 24.07 release.
For more information, see Darksite Upgrade of Trust Center.
Support for Uploading OTA packages to Darksite Trust Center
As Darksite Trust Center operates without internet connectivity, automatic OTA updates are not possible. Version 25.03 addresses this limitation by introducing a new command for managing firmware within the Trust Center. Administrators can now download as well as upload OTA packages to the Trust Center server without the need for opening an internet connection.
For more information see the following topics:
MariaDB Requirement Removed
In version 25.03, MariaDB has been merged into MongoDB. As a result, MariaDB is no longer deployed with the Trust Center. This simplifies end-user management of persistent stores and reduces memory and CPU footprint within the Trust Center.
Other Update
To limit the amount of sensitive data saved into Anyware Trust Center support bundles, the auto-generated Trust Center admin password, typically used as the default password, will no longer be saved to the configuration file. This limits the exposure of sensitive data, and prevents its accidental access.
25.03.1
Version 25.03.1 of the Anyware Trust Center is a maintenance release that replaces and deprecates 25.03.0. Additionally, it includes the following:
Support for MongoDB 5.x
Trust Center has updated it's internal Mongo DB instance to version 5.x, which requires the AVX CPU extension. Therefore, machines without AVX support can no longer successfully deploy a new Trust Center or upgrade an existing Trust Center to 25.03.0.
Previous Releases in This Version
25.03.0
Version 25.03.0 of the Anyware Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following:
Support for Imprivata Authentication
Version 25.03 of the Anyware Trust Center supports Imprivata OneSign for authenticating Trusted Zero Clients connecting to Horizon hosts. Imprivata OneSign enables users to access corporate networks, desktops, and applications with a single sign on. This reduces the need for maintaining separate passwords and prevents unauthorized access.
For more information, see Enabling Imprivata Authentication.
Trust Center Installation with DISA STIGs
In version 25.03, support has been added to enable the installation of the Trust Center on servers and virtual machines that comply with the security policies and configurations recommended by the US DOD Cyber Exchange. For this purpose, a new configuration called `fapolicyd` has been added, which allows the Trust Center components to run on servers that adhere to STIG requirements. For more information see Trust Center Installation with DISA STIGs.
SIPR/NIPR Network Migration
In version 25.03, support has been added for securely migrating Trusted Zero Clients between SIPR, NIPR, and insecure networks. When re-commissioning a Trusted Zero Client for use on a SIPR/NIPR or insecure network, specific steps must be followed to completely erase all local data and configurations. This prevents accidental or malicious access to critical data during network migrations, and ensures compliance with security recommendations.
Support for Darksite Upgrades
Version 25.03 now supports upgrade of Trust Center that does not have a connection to the public internet. Upgrading a dark site requires a temporary internet-connected machine, which downloads the required packages to create an upgrade bundle. The upgrade bundle is transferred to the dark site machine and used for upgrading Trust Center.
The dark site installer for 25.03 also includes a few changes from how the commands are run, from the original 24.07 release.
For more information, see Darksite Upgrade of Trust Center.
Support for Uploading OTA packages to Darksite Trust Center
As Darksite Trust Center operates without internet connectivity, automatic OTA updates are not possible. Version 25.03 addresses this limitation by introducing a new command for managing firmware within the Trust Center. Administrators can now download as well as upload OTA packages to the Trust Center server without the need for opening an internet connection.
For more information see the following topics:
Other Update
To limit the amount of sensitive data saved into Anyware Trust Center support bundles, the auto-generated Trust Center admin password, typically used as the default password, will no longer be saved to the configuration file. This limits the exposure of sensitive data, and prevents its accidental access.
25.03.0
Version 25.03.0 of the Anyware Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following:
Support for Imprivata Authentication
Version 25.03 of the Anyware Trust Center supports Imprivata OneSign for authenticating Trusted Zero Clients connecting to Horizon hosts. Imprivata OneSign enables users to access corporate networks, desktops, and applications with a single sign on. This reduces the need for maintaining separate passwords and prevents unauthorized access.
For more information, see Enabling Imprivata Authentication.
Trust Center Installation with DISA STIGs
In version 25.03, support has been added to enable the installation of the Trust Center on servers and virtual machines that comply with the security policies and configurations recommended by the US DOD Cyber Exchange. For this purpose, a new configuration called `fapolicyd` has been added, which allows the Trust Center components to run on servers that adhere to STIG requirements. For more information see Trust Center Installation with DISA STIGs.
SIPR/NIPR Network Migration
In version 25.03, support has been added for securely migrating Trusted Zero Clients between SIPR, NIPR, and insecure networks. When re-commissioning a Trusted Zero Client for use on a SIPR/NIPR or insecure network, specific steps must be followed to completely erase all local data and configurations. This prevents accidental or malicious access to critical data during network migrations, and ensures compliance with security recommendations.
Support for Darksite Upgrades
Version 25.03 now supports upgrade of Trust Center that does not have a connection to the public internet. Upgrading a dark site requires a temporary internet-connected machine, which downloads the required packages to create an upgrade bundle. The upgrade bundle is transferred to the dark site machine and used for upgrading Trust Center.
The dark site installer for 25.03 also includes a few changes from how the commands are run, from the original 24.07 release.
For more information, see Darksite Upgrade of Trust Center.
Support for Uploading OTA packages to Darksite Trust Center
As Darksite Trust Center operates without internet connectivity, automatic OTA updates are not possible. Version 25.03 addresses this limitation by introducing a new command for managing firmware within the Trust Center. Administrators can now download as well as upload OTA packages to the Trust Center server without the need for opening an internet connection.
For more information see the following topics:
Other Update
To limit the amount of sensitive data saved into Anyware Trust Center support bundles, the auto-generated Trust Center admin password, typically used as the default password, will no longer be saved to the configuration file. This limits the exposure of sensitive data, and prevents its accidental access.
24.10.2
Version 24.10.2 of the Anyware Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following features and changes:
Support for Imprivata Authentication
Version 24.10.2 of the Trust Center supports Imprivata OneSign Single Sign-On for authenticating Trusted Zero Clients connecting to Horizon hosts. Imprivata OneSign enables users to access corporate networks, desktops, and applications with a single sign on. This reduces the need for maintaining separate passwords and prevents unauthorized access.
For more information, see Enabling Imprivata Authentication.
Trust Center Installation with DISA STIGs
In version 24.10.2, support has been added to enable the installation of the Trust Center on servers and virtual machines that comply with the security policies and configurations recommended by the US DOD Cyber Exchange. For this purpose, a new configuration called fapolicyd has been added, which allows the Trust Center components to run on servers that adhere to STIG requirements. For more information see Trust Center Installation with DISA STIGs.
SIPR/NIPR Network Migration
In version 24.10.2, support has been added for securely migrating Trusted Zero Clients between SIPR, NIPR, and insecure networks. When re-commissioning a Trusted Zero Client for use on a SIPR/NIPR or insecure network, specific steps must be followed to completely erase all local data and configurations. This prevents accidental or malicious access to critical data during network migrations, and ensures compliance with security recommendations.
Note:
Support for RHEL 8 has been extended until the end of 2025.
24.10
Version 24.10 of the Trust Center contains bug fixes and stability enhancements. Additionally, it also includes the following features and changes:
Support for Kiosk Mode
Version 24.10 of the Trust Center introduces support for enabling the Kiosk mode in Trusted Zero Clients. This feature builds upon the existing Automatic login functionality, and allows for the creation of fixed purpose devices such as point-of-sale terminals and digital signs.
In Kiosk Mode, the process of connecting to remote hosts is simplified. End-users do not need to provide their credentials, and instead, only see a progress indicator while establishing a connection. The ability to bypass traditional login steps ensures that end-users experience a seamless login process.
For instructions on enabling Kiosk mode, see Enabling Kiosk mode.
Support for Configuring the Login Experience on Trusted Zero Clients
Trust Center 24.10 comes with the ability to control the login experience of the Trusted Zero clients. Depending on the configuration, Trusted Zero Clients can skip one or more of the following login steps:
- Connecting to a broker
- Providing user credentials
- Selecting a desktop
The ability to bypass one or more traditional login steps simplifies and streamlines the login process, and enhances the user experience.
For more information, see Configuring the Login Experience on the Trusted Zero Clients.
Management API Endpoint for Sorting
Version 24.10 introduces the following new query parameters for sorting:
sortKey
This represents the field to sort by
sortDirection (ASC or DESC)
This represents the sorting order
The parameters have been added to the GET /endpoints, GET /commands, and GET /assets routes.
The new query parameters enable sorting by a field or column of choice, making it easier to present data in a meaningful way.
Support for Deleting Endpoints
Trust Center version 24.10 now supports deleting endpoint twin records using the management API. You can delete an endpoint by sending a DELETE request to /api/v1/endpoints/:endpointId.
However, if an endpoint is connected to Trust Center, it will attempt to reconnect and recreate a new digital twin with empty properties, and therefore, cannot be directly removed with a DELETE request. To completely remove the endpoint, you must first factory reset the endpoint to disconnect it from Trust Center. Once this is done, use the DELETE API to remove the endpoint.
Support for Bulk Endpoint Commands
Trust Center version 24.10 API now supports a new route, POST / commands, to send the same command to multiple endpoints. Endpoints are selected by specifying tags in the request body. The command and payload is then sent to all endpoints matching the provided tags.
Support for Bulk Endpoint Updates
Trust Center version 24.10 API now supports a new route, PUT /endpoints, to update multiple endpoint desired or default properties. Endpoints are selected by specifying tags in the request body. The property value is then applied to all endpoints matching the provided tags at the specified property path.
24.07
Support for Automatic Login
The Trust Center can now configure Trusted Zero Clients to automatically login to remote desktops. This enables the clients to operate in environments where they're being used similar to a kiosk. This feature is useful in environments such as secure factory floors (CNC operators), advertisement boards, flight status boards in airports, point-of-sale terminals, and barcode scanner terminals.
Note: The Anyware Trust Center must be configured to enable users to automatically log in. Instructions for setting up the Trust Center are available in the Anyware Trust Center 24.07 Administrators' Guide.
24.03.2
Release 24.03.2 of the Anyware Trust Center is a maintenance release which replaces and deprecates 24.03.0. It includes the following:
Added product and board serial to endpoint static properties
properties/static/serialNumber is now deprecated. Instead, properties/static/productSerialNumber and properties/static/boardSerialNumber can now be used to obtain more specific serial information for Trusted Zero Clients.
Operational certificate renewal safety
Previously, when setting renewBefore to a value greater than the lifetime of the operational certificate, the Trusted Zero Client would continually renew the op cert making the endpoint appear to be unable to connect to the Trust Center. A safety has been put in place to ensure that if invalid renewal values are set, the Trust Agent will ignore and use a reasonable default.
Previous release information:
Release 24.03.0 of the Anyware Trust Center includes the following:
Static IP Support
You can now configure a Trusted Zero Client's IPv4 and IPv6 settings via the Trusted Zero Client's interface, or by pushing from the Anyware Trust Center.
Support for 802.1x
With this release, you can now manually provision Trusted Zero Client devices with certificates for networks which require 802.1x authentication. The method used to do this depends on your Endpoint Management System (EMS); refer to your manufacturer's documentation for more information.
Client Firmware Version Enforcement
A new Trusted Zero Client policy has been added that allows administrators to set a desired firmware version number, and then block new sessions for any Trusted Zero Client devices that are out of date.
Setting desired/trust/policies/version to the desired version number will enforce this policy.
Support for Darksite Installations
The Anyware Trust Center can now be installed in dark sites, which do not have a connection to the public internet. Installing in a dark site requires a temporary internet-connected machine, which downloads required packages and creates an installation bundle. The installation bundle is then transferred to the dark site machine and installed. For system requirements, see Dark Site System Requirements. For installation instructions, see Dark Site Installation.
Note: OTA updates to Trusted Zero Client devices in dark sites is not supported in this release.
24.03
Release 24.03 of the Anyware Trust Center includes the following:
Static IP Support
You can now configure a Trusted Zero Client's IPv4 and IPv6 settings via the Trusted Zero Client's interface, or by pushing from the Anyware Trust Center.
Support for 802.1x
With this release, you can now manually provision Trusted Zero Client devices with certificates for networks which require 802.1x authentication. The method used to do this depends on your Endpoint Management System (EMS); refer to your manufacturer's documentation for more information.
Client Firmware Version Enforcement
A new Trusted Zero Client policy has been added that allows administrators to set a desired firmware version number, and then block new sessions for any Trusted Zero Client devices that are out of date.
Setting desired/trust/policies/version to the desired version number will enforce this policy.
Support for Darksite Installations
The Anyware Trust Center can now be installed in dark sites, which do not have a connection to the public internet. Installing in a dark site requires a temporary internet-connected machine, which downloads required packages and creates an installation bundle. The installation bundle is then transferred to the dark site machine and installed. For system requirements, see Dark Site System Requirements. For installation instructions, see Dark Site Installation.
Note: OTA updates to Trusted Zero Client devices in dark sites is not supported in this release.
23.12.1
Release 23.12.1 of the Anyware Trust Center is a maintenance release which replaces and deprecates 23.12.
It includes the following:
- Bug fixes and security updates.
Previous release information:
Release 23.12 of the Anyware Trust Center includes the following:
Endpoint Maximum Increased
Performance improvements in 23.12 allow the Anyware Trust Center to support 5,000 endpoints (previously, the maximum was 1,000).
Minimum Requirements Lowered
Performance improvements also allow the Anyware Trust Center to use half the previous vCPU and RAM specification; the Anyware Trust Center now requires at least 4 vCPUs and 16GB of RAM (previously, the minimum was 8 vCPUs and 32GB of RAM). See System Requirements for more information.
New Device Timeout Policy
You can now set a policy for the length of time that a Trusted Zero Client can remain disconnected from a Anyware Trust Center before it becomes untrusted.
23.12
Release 23.12 of the Anyware Trust Center includes the following:
Endpoint Maximum Increased
Performance improvements in 23.12 allow the Anyware Trust Center to support 5,000 endpoints (previously, the maximum was 1,000).
Minimum Requirements Lowered
Performance improvements also allow the Anyware Trust Center to use half the previous vCPU and RAM specification; the Anyware Trust Center now requires at least 4 vCPUs and 16GB of RAM (previously, the minimum was 8 vCPUs and 32GB of RAM). See System Requirements for more information.
New Device Timeout Policy
You can now set a policy for the length of time that a Trusted Zero Client can remain disconnected from a Anyware Trust Center before it becomes untrusted.
23.08
Anyware Trust Center 23.08 is a minor release that contains bug fixes, improved operating system support, and process improvements. There are no feature changes in this release.
Support added for RHEL 9 and Rocky Linux 9
This release adds support for the Anyware Trust Center on RHEL 9 and Rocky Linux 9.
Installation process improvements
We've revised our documentation and website flow to alleviate confusion around setting up the Anyware Trust Center domain name. Previously, we used the term FQDN to describe the domain name and neglected to provide examples that clarify the actions you need to take. We've changed those FQDN references to "domain name", added examples, and also added a live preview feature to the website that shows exactly which subdomains you need to configure based on your input.

23.06.1
Release 23.06.1 of the Anyware Trust Center is a maintenance release which replaces and deprecates 23.06.
It includes the following:
- Fixes a bug that caused endpoint internationalization properties to be incorrectly validated by the Management API, resulting in an error. This has been fixed.
Previous release information:
This is the public release of the Anyware Trust Center. For feature support, system requirements, and installation instructions, please refer to the Anyware Trust Center Administrators' Guide. The download script for the Anyware Trust Center is available here. Downloading the Anyware Trust Center requires a valid Anyware Trust Center subscription.
For information about Trusted Zero Clients, see the Trusted Zero Client Administrators Guide.
23.06
This is the public release of the Anyware Trust Center. For feature support, system requirements, and installation instructions, please refer to the Anyware Trust Center Administrators' Guide. The download script for the Anyware Trust Center is available here. Downloading the Anyware Trust Center requires a valid Anyware Trust Center subscription.
For information about Trusted Zero Clients, see the Trusted Zero Client Administrators Guide.
23.04
This is a private beta release of the Anyware Trust Center. Availability of this release is by invitation; contact us for more information.
Deploying the Anyware Trust Center
These instructions will guide you through creating a VM, downloading the installer, and deploying an Anyware Trust Center on a single machine.
Deploy a VM
First, create a new VM that will host the Anyware Trust Center.
The Trust Center requires:
- RHEL 8 or Rocky Linux 8
- 8 vCPUs
- 32GB RAM
- 120GB+, with 80GB +free disk space available on /var
- IP network accessible by your endpoints, with DNS configured as described next. The Anyware Trust Center does not support connections via raw IP addresses.
Choose an FQDN
The Trust Center requires a FQDN for connections. You'll use this value in multiple locations during setup, so record the value and be ready to copy it.
Create DNS Records
Once the machine is up, create the following DNS A records that point to it. In each of these entries, <domain> is the FQDN you chose in the previous step.
trust-center.<domain>endpoint-connector.<domain>ota.<domain>register.<domain>
In addition, if you wish to support automatic Trust Center discovery by endpoints, you will need to create a CNAME record redirecting "anywaretrustcenter" to "register.<domain>"
Download and Install the Anyware Trust Center
To install the Anyware Trust Center, you must have an account on our support site (https://help.teradici.com). You can create one from the login screen if you don't already have one.
To download the installer:
- Go to https://docs.teradici.com/find/product/anyware-trusted-endpoints/2023.04/anyware-trust-center.
- If you are not already logged in, click Log in to download to log in.
- Click on
 .
. - Accept the license agreement:

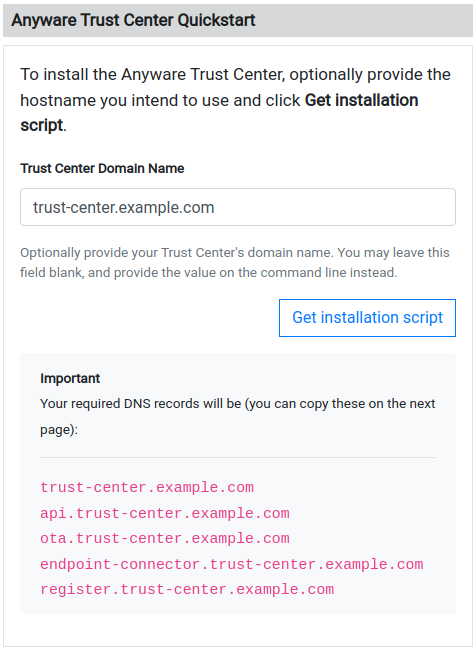
- Paste in your FQDN, recorded earlier, in the Trust Center Hostname (FQDN) field, and click Get installation script:

Note: You can leave the FQDN field blank; if you do, the installation command will still be generated, but you will have to manually replace the placeholder value with the actual FQDN before executing it. - Copy the entire command displayed next. There are two parts, and both are required: a curl command that downloads the installation script, and another command that executes it.
A valid Trust Center download link will look like this:curl -sSL https://dl.teradici.com/{token}/trust-center/raw/names/trust-center-tgz/versions/23.04.0/trust-center_23.04.0.tar.gz | tar -xz && sudo ./trust-center-ctl install --fqdn {trust-center-FQDN} --token {jwt token}
Copy the entire link, which will be used on the Trust Center VM when it is set up.
Important: The generated command is valid for 2 hours, after which installation will fail. If that occurs, return to the download page and generate a new command.When executed, the command will do the following:
- Downloads the installer executable in an archive format
- Unzips the installer
- Runs the installer as a root user, passing in 2 required flags:
- fqdn - the value must be a valid fully qualified domain name, and should point to the location where the Trust Center is installed.
- token - this value is provided by support, and should not be modified. It is also only valid for 2 hours.
Installing the Anyware Trust Center
- On the Trust Center machine, navigate to a working directory. You can create a new one or use an existing one to install the Trust Center.
- Navigate to your working directory using a terminal window (command line).
- Paste the download link you copied previously into the terminal window and press Enter to execute it.
The installation will take up to 15 minutes to complete; there will be periods of time where the process stops printing messages to the terminal and may appear to hang. This is normal.
After Installing
Once installation is complete, you can set up your Management Console to interact and manage Trusted Zero Clients through your Trust Center.
Refer to the API documentation installed with the Trust Center for complete details.
Note: the administrator password is now automatically generated by the Trust Center installer, and has the ability to create service account keys. The Trust Center API documentation does not show this yet. The generated password is placed in a file in your installation working directory:
<current folder>/config.yaml
global:
images:
registry: "docker.cloudsmith.io/teradici/trust-center"
username: "teradici/trust-center"
password: <repository password>
tc:
domain: <your domain>
password: <this is the auto-generated password>
endpointUpdate:
accessKey: <repository password>
repository: "teradici/trusted-zero-client"
Upgrading to a New Version
To upgrade the current running installation of the Trust Center, obtain a newer download link from the website. Make sure the package version is newer than your installed version. Download links look like this:
curl -sSL https://dl.teradici.com/{a token}/trust-center/raw/names/trust-center-tgz/versions/23.04.1/trust-center_23.04.1.tar.gz
In this example, the command will download version 23.04.1 of the Trust Center.
Then:
- Download the new package to the same installation directory you used for your original installation.
- Open a terminal window and navigate to your installation directory
- Run the following command:
./trust-center-ctl upgrade
Troubleshooting
Support Bundle
If you encounter problems while running the Anyware Trust Center, you can generate a support bundle to help us diagnose and troubleshoot the issue. Support bundles capture the state of the Trust Center and related services and log files.
To generate a support bundle:
- Open a terminal window and navigate to your Trust Center installation directory.
- Run the following command:
sudo ./trust-center-ctl diagnose --support-bundle
The support bundler will generate an archive and place it in your working directory. - Provide this generated support bundle to our support team.