Steps to join/add RHEL 8 to Active Directory Services (Windows Server 2019)
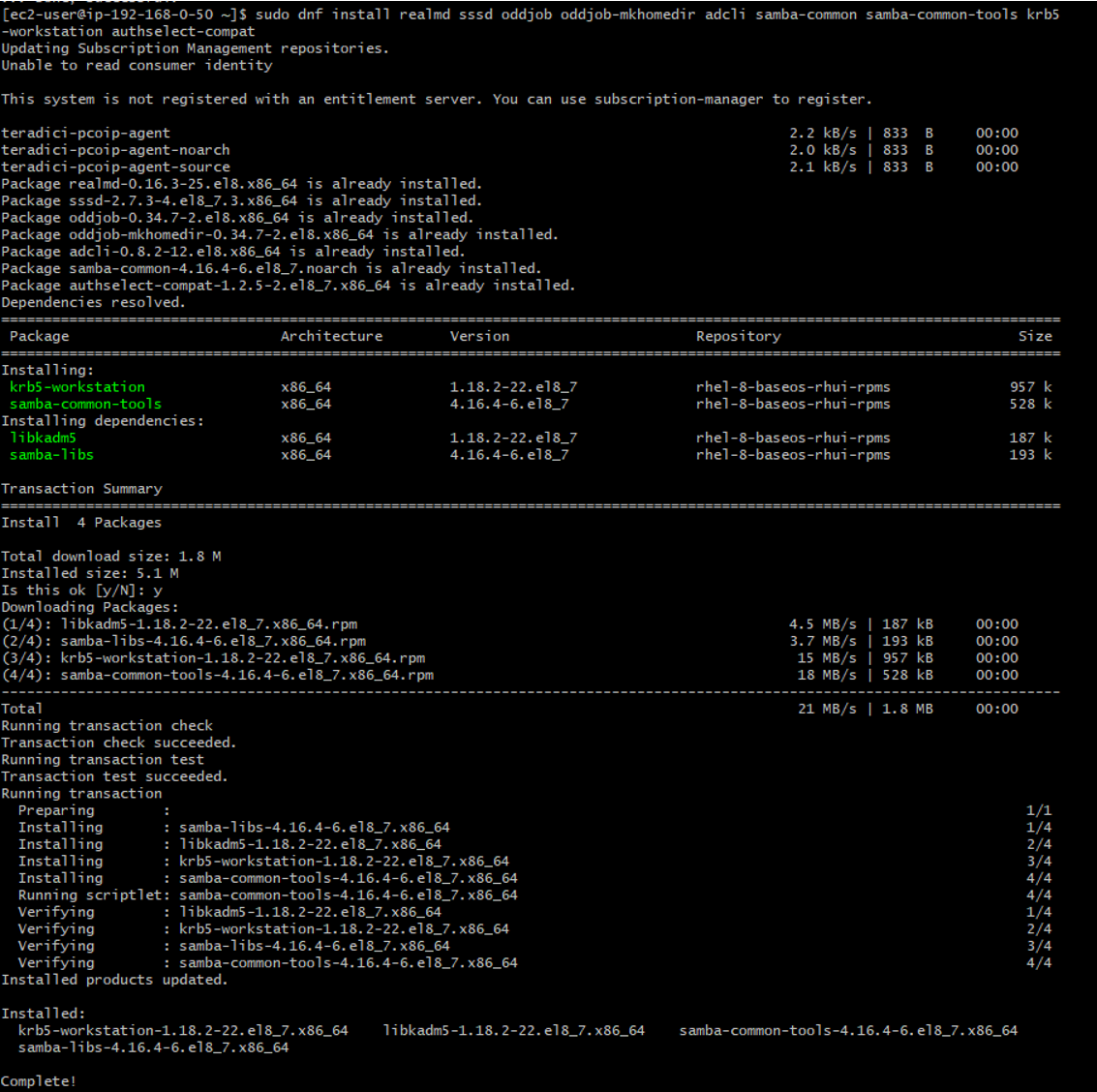
1. We will now install all required packages for our domain join adventure
sudo dnf install realmd sssd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5
yum -y install samba samba-client
yum -y install samba-winbind samba-winbind-clients
yum -y install krb5-workstation
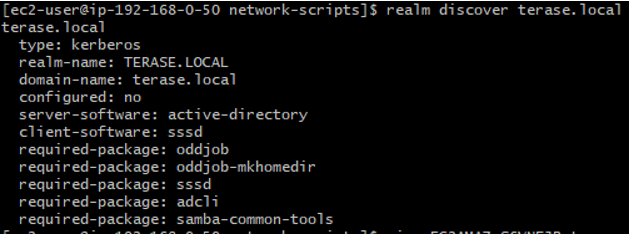
2. Check if AD domain discovery is successful.
sudo realm discover terase.local
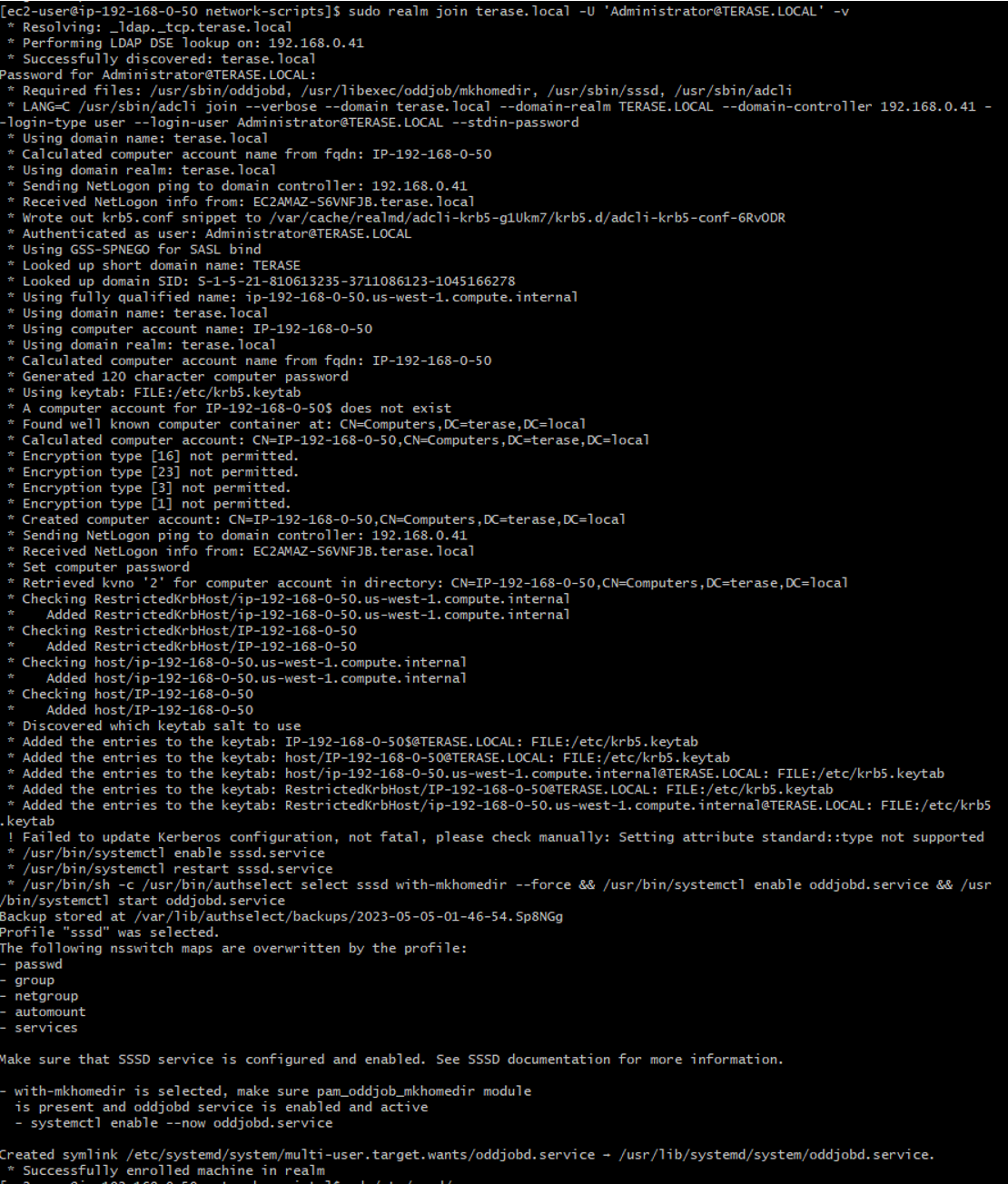
3. Change Administrator if the account name of your domain admin is different.
sudo realm join terase.local -U 'Administrator@TERASE.LOCAL' -v
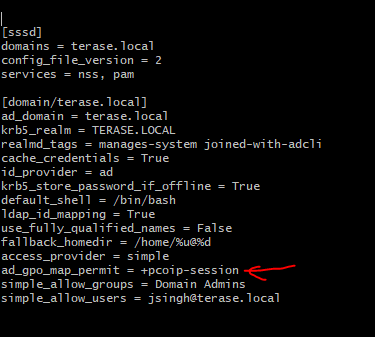
4. Setting up sssd: (To discover and join windows domain) sudo nano /etc/sssd/sssd.conf
Don’t forget to add the line end of the conf file before making the pcoip session (ad_gpo_map_permit = +pcoip-session)
sudo nano /etc/sssd/sssd.conf
[sssd]
domains = terase.local
config_file_version = 2
services = nss, pam
[domain/terase.local]
default_shell = /bin/bash
ad_server = terase.local
krb5_store_password_if_offline = True
cache_credentials = True
krb5_realm = TERASE.LOCAL
realmd_tags = manages-system joined-with-adcli
id_provider = ad
ldap_sasl_authid = IP-192-168-0-18$
fallback_homedir = /home/%u@%d
ad_domain = terase.local
use_fully_qualified_names = False
ldap_id_mapping = True
access_provider = ad
ad_gpo_map_permit = +pcoip-session
After making the changes make sure restart the sssd services.
sudo systemctl restart sssd
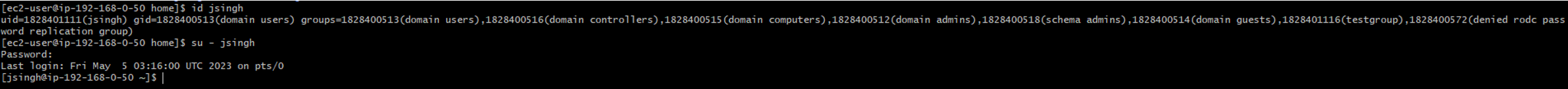
5. After doing all the configuration search for the user
#id Administrator@terase.local
#Su - Administrator
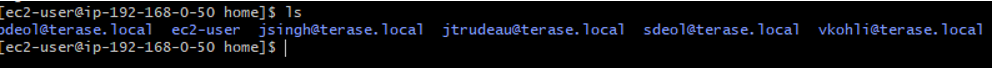
8. Before to make a pcoip session please make sure the user is already in the /home directory!
9. Practical way would be, to deny login to all, and then add permits to exceptions, so that would look like this
sudo realm deny --all
sudo realm permit Administrator@terase.local
sudo realm permit -g 'Domain Admins'
10. You can also permit all, and add multiple user or groups using one line, so that would look like
sudo realm permit --all
sudo realm permit Administrator@terase.local jsingh@terase.local
sudo realm permit -g 'Domain Admins' 'Users'